Installing Wireshark. Installing Wireshark is an easy process. It’s free tool across different platforms, and here is how you can download and install it. Wireshark El Capitan Mac OS X Due Being the successor of OS X Yosemite, it mainly focuses on stability, performance, and security. It was the final version that was released beneath the name OS X, its successor, Sierra, was given the name under Mac OS X due to the reason that OS X is now named Mac OS. Download the latest version of Wireshark for Mac. Capture and analyze data packets from any network. Wireshark is a protocol analyzer based on pcap libraries. To install Wireshark on Mac you first need to download an installer. To do this, download an installer such as exquartz. Once you’ve done this, open the Terminal and input the following command. Download and install the Wireshark software:. Go to and download and install the Wireshark binary for your computer. The Wireshark FAQ has a number of helpful hints and interesting tidbits of information, particularly if you have trouble installing or running Wireshark.
Table of Contents
Quicklinks: Wireshark: Installation Chapter
Install Wireshark with a Package Manager
Where available, prefer your package manager. Note that Wireshark v3 is not currently available on many Linux package managers (this will change soon).
| System | Install Command | Latest Version |
|---|---|---|
| Linux | $PkgManager install wireshark | 2.6.8 and below |
| Macos | brew install --cask wireshark | 3.0.2 |
| Windows | choco install wireshark | 3.0.2 |
Installing tshark Only
Note: If you have not used tshark before, you should install the wiresharkpackage as above before limiting yourself to the CLI.
If you want to install just tshark and no Qt/GUI components, this is possible onvarious linux distributions. The package is called tshark or wireshark-clidepending on the platform.
Install the package tshark:
- Alpine >= 3.9
- Debian >= 9
- FreeBSD >= 11
- OpenMandriva >= 3.0
- PCLinuxOS
- Ubuntu >= 14.04
Install the package wireshark-cli.
- Arch Linux
- CentOS >= 8
- Fedora >= 30
- RedHat
For up-to-date package information, check the package registry fortshark andwireshark-cli
Install with a package
To get the most up-to-date official packages, visit Wireshark’s Download Page.
There are multiple packages available from Wireshark’s download page. The installation is simple, but make sure to check the components that.
Install from Source
Linux currently does not have packages in official repositories, so if you want the latest, you have to build it (this will likely change soon).
Linux, v3.0.0
You need to install from source to get v3 on Linux. This will get a clean system on Ubuntu18.04 to an install: Etab civil engineering software free full version.
If you are on a different system, only the last 3 steps apply. Make sure thatyou’ve satisfied the other dependencies. cmake will kindly let you know if youhaven’t.
Check Installation
1. Check Version
If the version doesn’t match the expected one, you may want toinstall from source or use Wireshark’s download page.
2. Check Interfaces
tshark -D will list all interfaces that it sees.
dumpcap does not see and cannot capture on virtual interfaces. This means that dumpcap -D will show fewer interfaces than tshark -D.
Different systems will report different interfaces. tshark will treat the first interface as the default interface and capture from it by default.In other words, tshark aliases to tshark -i 1. You may need to use sudo depending on your installation.Default interfaces on installs of macos, windows, linux, and freebsd are shown below.
3. Test Live Capture
Entering the tshark command should immediately start capturing packets on the default interface. If you donot see packets, check out Choosing an Interface.
4. Make Sure Utilities are on $PATH
Setting up your environment should be done once and done well. There are a coupleAdditional work is usually necessary to make sure all utilities are on the path.
bash
You can verify whether all are installed with the following:
If a util is installed but not on your $PATH, you can use find / -name $util 2>/dev/nullto find out where it may be. For example, on Linux for 3.0.0, extcap tools areat /usr/lib/x86_64-linux-gnu/wireshark/extcap. To add them to your path, useecho 'export PATH=$PATH:$folder' >> ~/.profile.
Powershell on Windows
Currently, extcap utils need to bemoved from Wiresharkextcap => Wiresharkto be useable. If you have not added your %Program Files% to your $PATH, you cando that with an Admin user:
[Environment]::SetEnvironmentVariable('PATH', '$PATH;$ENV:ProgramFilesWireshark', 'Machine')
You will need to reopen Powershell for the $PATH to be updated.
This article will explain how to use wireshark to capture TCP/IPpackets. Specifically I will show how to capture encrypted (HTTPS)packets and attempt to document the 'dance' a client and server do tobuild an SSL tunnel.
What is Wireshark?
Wireshark is a network protocol analyzer for Windows, OSX, and Linux. Itlets you capture and interactively browse the traffic running on acomputer network. Similar software includes tcpdump on Linux.
Install Wireshark
First step, acquire Wireshark for your operating system.
Ubuntu Linux:sudo apt-get install wireshark

Windows or Mac OSX: search for wireshark and download the binary.
How to capture packets
This is Wireshark's main menu:
To start a capture, click the following icon:
A new dialog box should have appeared. Click start on your preferredinterface:
You are now capturing packets. The packet information is displayed inthe table below the main menu:
Now browse to an HTTPS website with your browser. I went tohttps://linkpeek.com and after the page completely loaded, I stopped theWireshark capture:
Depending on your network, you could have just captured MANY packets. Tolimit our view to only interesting packets you may apply a filter.Filter the captured packets by ssl and hit Apply:
Now we should be only looking at SSL packets.
Next we will analyze the SSL packets and answer a few questions
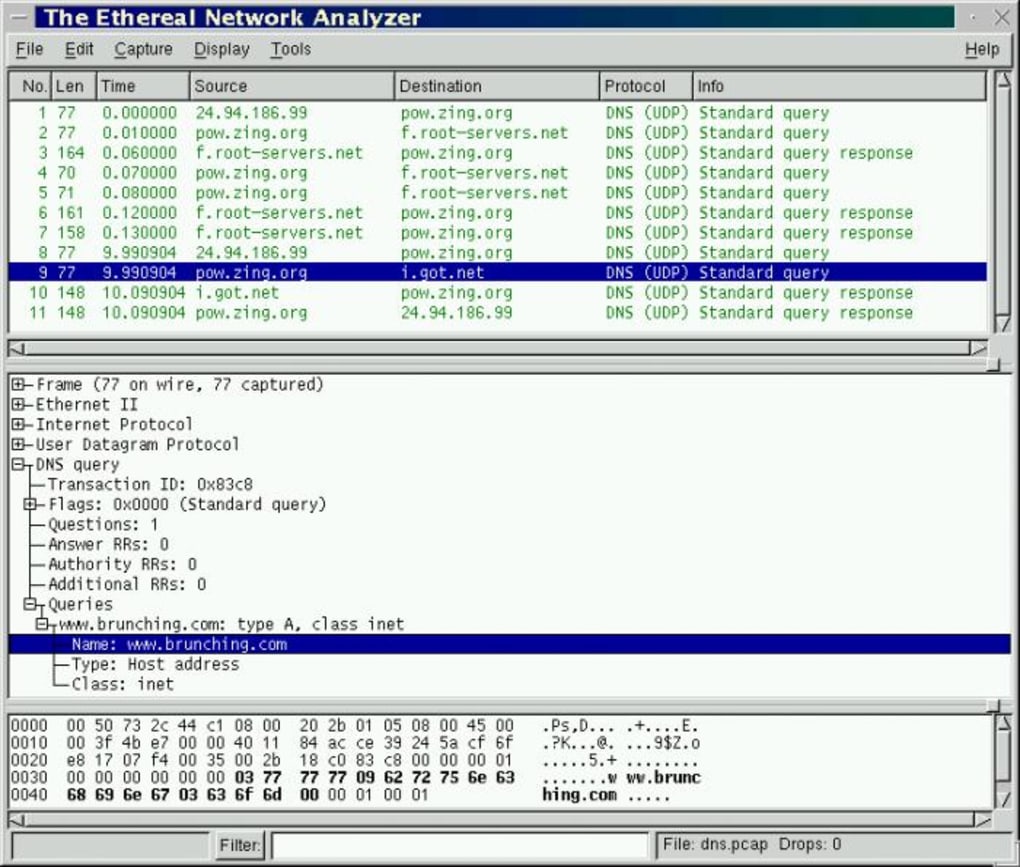
1. For each of the first 8 Ethernet frames, specify the source ofthe frame (client or server), determine the number of SSL records thatare included in the frame, and list the SSL record types that areincluded in the frame. Draw a timing diagram between client and server,with one arrow for each SSL record.

2. Each of the SSL records begins with the same three fields (withpossibly different values). One of these fields is “content type” andhas length of one byte. List all three fields and their lengths.
02 ninja 500 repair manual. ClientHello Records
Wireshark Download Old Version
ServertHello Records
Wireshark Download Mac Os X
Wireshark Download For Mac
Looking for a better comment system?
You should try Remarkbox — a hosted comment service that embeds in your pages to keep the conversation in the same place as your content. It works everywhere, even static sites!